...
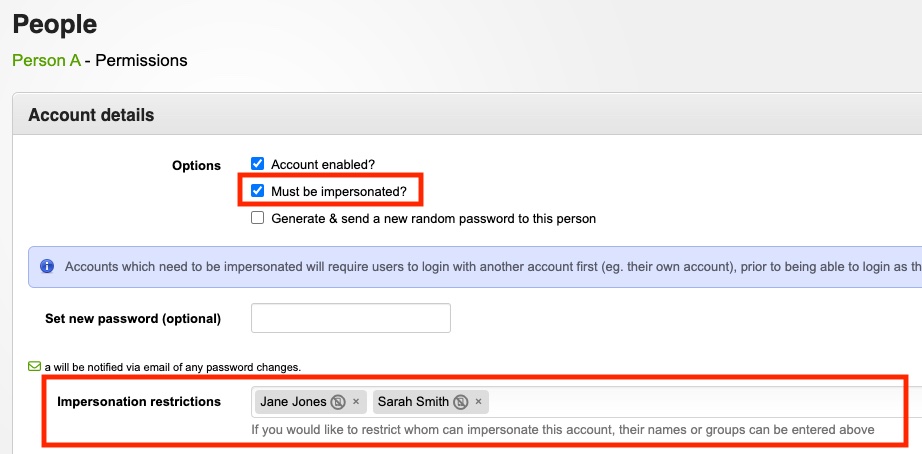
If the account being setup is role-based (eg. Supervisor), rather than for a particular individual, you can set up the account so it can only be used when someone has already logged in through their own account - eg. John Smith would need to first log in to the system using his own username and password, and only then can he log in to the 'Supervisor' account he would like to use to obtain further access. This means that you can have a single high-privilege account that is shared between multiple staff, while still being able to audit system changes to a specific person.
Gliffy
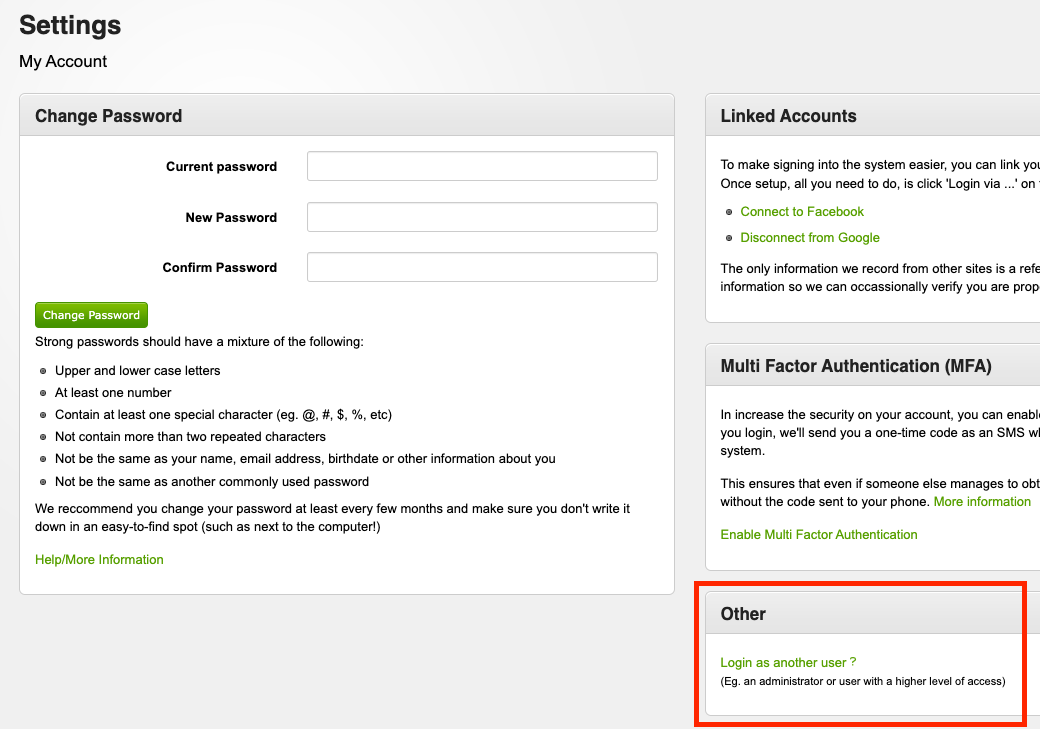
To log into an impersonated account, go to 'Settings' > 'My Account & Password', and then click 'Login as another user' on the right-hand side of the page.
...
Whenever 'impersonation restrictions' are entered, rather than allowing anyone with the username and password to impersonate the account, the system will restrict whom can impersonate the account to only those people whom meet at least one of the requirements (eg. being the user whom is named, or being part of the group listed).
...
Login as your staff & volunteers
You can also use account impersonation to diagnose issues your staff and volunteers might have come across.
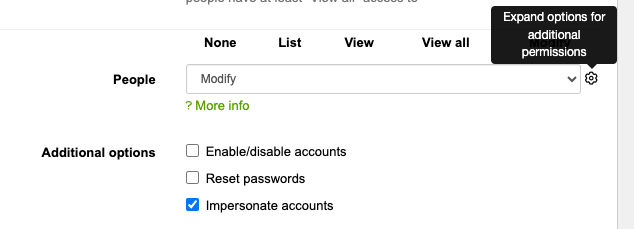
Required permissions: the account you're using needs to have administrator rights to permissions to impersonate the accounts, in all groups the person you wish to impersonate is part of.
Administrator access also gives you "impersonate accounts" access, but your account still needs permissions in all groups the person you're trying to impersonate is part of.
Eg. if Person A (you) is logged in, and would like to impersonate Person B (part of Groups A, B, and C), then Person A needs to have administrator access to impersonation permissions in at least groups A, B, and C (at least). This is to ensure there is no security risk to the information Person B has access to.the user can't inadvertatly gain access to additional groups they wouldn't have otherwise had access to (ie. groups Person B is part of).
Auditing: Note that all actions you take as 'Person B' will be logged as per normal, along with a note indicating you (Person A) were logged in at the time.
How?
The 'Impersonate' button at the top-right of the permissions page for a person (eg. Person B in this instance) will log you into their account.
...